Advanced cluster node failure detection enhanced with HMC REST interface
Introduction
IBM® PowerHA® for i Standard Edition enhanced advanced node failure detection to support a new representational state transfer (REST) interface. The Hardware Monitor Console (HMC) is being updated to replace the existing Common Information Model (CIM) server with a new representational state transfer (REST) based interface. HMC version V8R8.5.0 is the last version of HMC to support the CIM server, and is the first version of HMC to support all REST API functions that are required by IBM PowerHA SystemMirror® for i licensed program. This function is provided through a new function PowerHA PTF.
Software Requirements
- 5770-SS1 Base operating system option 3 - Extended Base Directory Support
- 5770-SS1 Base operating system option 33 - Portable Application Solutions Environment
- 5733-SC1 - IBM Portable Utilities for IBM i (Only required for initial configuration of a cluster monitor.)
- 5733-SC1 option 1 - OpenSSH, OpenSSL, zlib (Only required for initial configuration of a cluster monitor.)
- 5770-HAS IBM PowerHA for i LP
- HMC version V8R8.5.0 or later. This is the first version of HMC to support the REST server
- TLS V1.2 Enabled (See: http://www-01.ibm.com/support/docview.wss?uid=nas8N1020876)
- PowerHA for i new function cluster monitor HMC REST support PTFs:
- V7R1 - PowerHA PTF Group SF99706 level 13
- V7R2 - PowerHA PTF Group SF99776 level 6
- V7R3 - PowerHA PTF Group SF99876 level 3
Configuring advanced node failure detection on hardware management console (HMC) with REST server
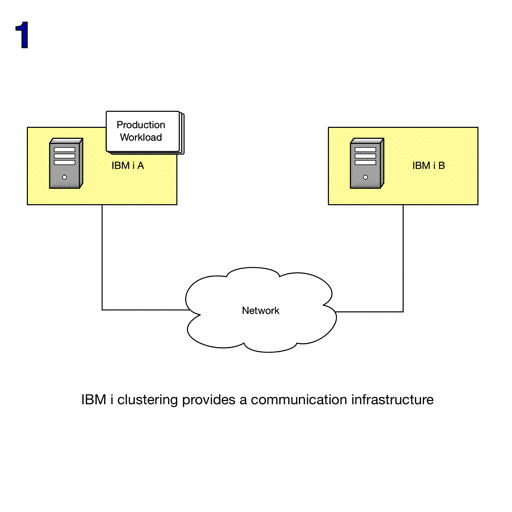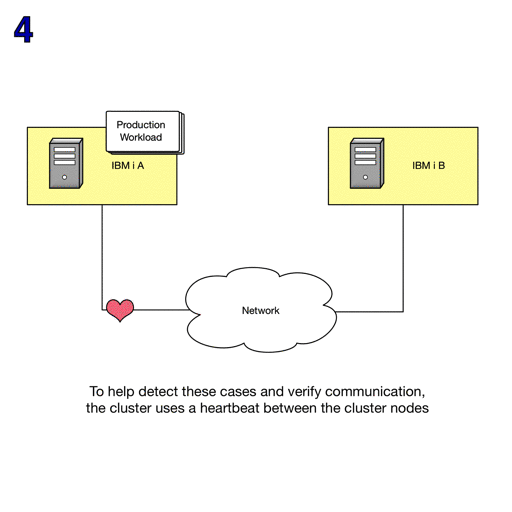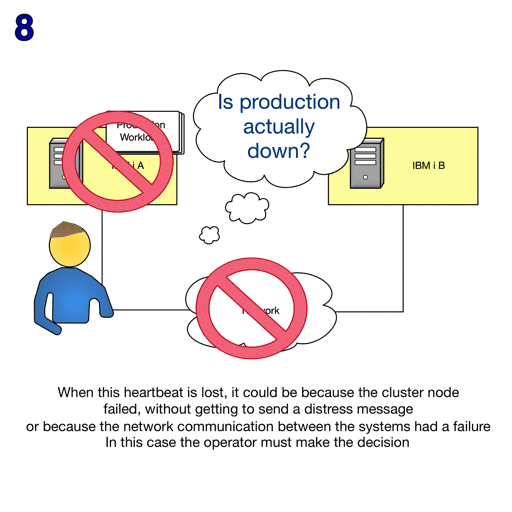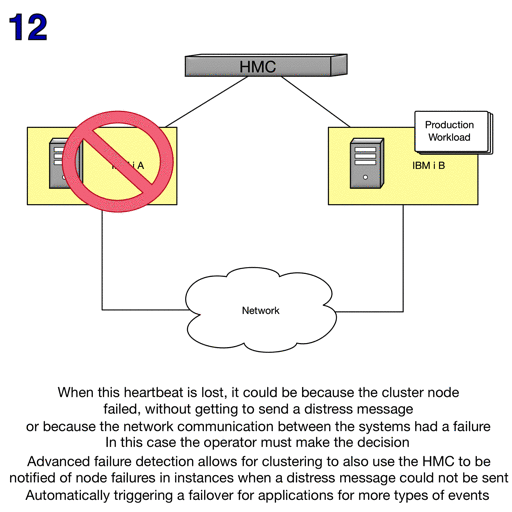
The Advanced node failure detection function can reduce the number of failure scenarios that result in cluster partitions.
A Hardware Management Console (HMC) can be used with advanced node failure detection to prevent cluster partitions when a cluster node has actually failed.
Before you begin
Consult the requirements and restrictions before setting up advanced node failure detection in a cluster:
Using HMC with a Representational state transfer (REST) server requires a HMC minimum version of V8R8.5.0 to implement and configure advanced node failure detection. See Planning advanced node failure detection for hardware and software requirements.
The Add cluster monitor (ADDCLUMON) command must be used with the representational state transfer (REST) server. The PowerHA® graphical interface does not support REST servers.
Check the QSSLPCL system value. Verify that it is set correctly for the release currently running.
NOTE: An incorrect value in QSSLPCL may result in a CPFBBCB diagnostic message with reason code 4.
To allow a an HMC using REST server to notify IBM i cluster nodes of sudden partition changes or system failures, communication between the HMC and the cluster nodes must be enabled. A digital certificate from the HMC is required and a secure certificate keystore and access to the certificate, if necessary, must be created. This certificate from the HMC is copied and installed on every node in the cluster that requires monitoring.
The setup instructions include steps for creating a *SYSTEM certificate keystore. This keystore may have already been created. If so, the password is required. Ask your IBM® i administrator for the keystore and access information.
About this task
These steps guide you through obtaining the digital certificate of your HMC, storing it and referencing it to allow advanced node failure detection for the cluster node.
IMPORTANT: This guide describes steps making use of features of both HMC and of the Digital Certificate Manager. Changes to either of these products may cause portions of this guide to become invalid. If you suspect such changes are preventing you from following the steps outlined in this guide successfully, contact your technical support provider.
Procedure
Create a *SYSTEM certificate store to hold the digital certificates
To create the *SYSTEM certificate store, use the following steps:
Determine the type of Certificate Used by the HMC
Importing Certificates into the System Certificate Store
Follow the instructions depending on the type of certificate used by the HMC.
Importing a Trusted Certificate into the System Certificate Store
To import a trusted certificate, follow the instructions in the IBM Documentation for Digital Certificate Manager.
Results
The selected security certificate is imported into the certificate store.
What to do next
After importing the certificates, sign on to your IBM i and use the command line to run the Add cluster monitor (ADDCLUMON) command to run the cluster configuration steps. For additional information about ADDCLUMON, see the Add Cluster Monitor (ADDCLUMON) command in the Knowledge Center.
More Information
For more information see the following topics in the IBM i Knowledge Center:
Privacy Policy | Cookie Policy | Impressum
From time to time, this website may contain technical inaccuracies and we do not warrant the accuracy of any posted information.
Copyright © Fortra, LLC and its group of companies. All trademarks and registered trademarks are the property of their respective owners.